You’ve always felt like you needed a little more home security, and pondered whether or not the hassle of a security camera would be worth the return. One day you finally give in and purchased a camera, or camera system, and thought that the peace of mind that being able to check on your home while away from over the internet is a convenient feature.
Not so much.
Thanks to Shodan, I can show you how easy it is to gain access to IP cameras. I will not login to any of the cameras for legal reasons, but I hope to leave you with an understanding of how easy it is to use a device intended for the security of someone to be used against them when the time is not taken to secure a device or devices properly. There are types of cameras where no login is required and can be viewed by merely going to an IP address or URL.
Shodan works by looking at the text in the HTTP header of Internet-connected devices and is covered at length here.
We begin by entering the search phrase – title:”IP CAMERA.”
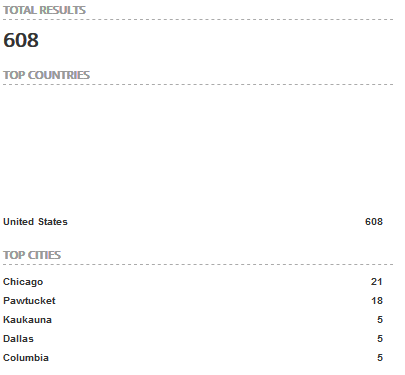
The above query returns a total of 4,390 results with the US, Germany, Republic of Korea, Italy, and India as the top countries.
Drilling down into the result by selecting the United States the top cities include Chicago, Pawtucket (really?), Kaukauna (where?), Dallas, and Columbia.
Taking the first search result we can see the login page for the camera, and from here you try a combination of different usernames and passwords. GeoVision Inc. IP cameras appear to be the most popular by far.
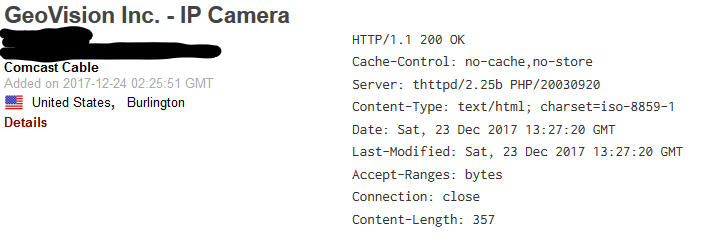
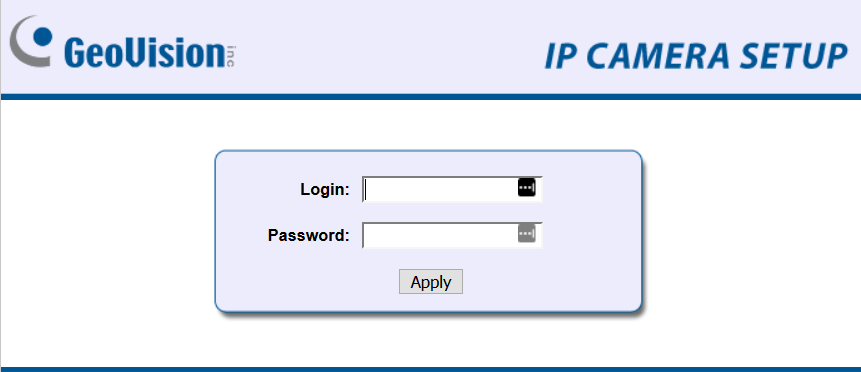
I wish securing Internet-of-Things devices were as easy as changing the default password, but we must also contend with poor coding that leaves these operating system riddled with vulnerabilities.
What makes matters worse is security vulnerabilities are rarely fixed, and when security vulnerabilities are fixed you’re usually not notified of a new firmware version. If you are fortunate enough to have an IoT device from a manufacturer that sends notifications for new firmware, they typically address only the most severe vulnerabilities that are made public.
Yes, there are many vulnerabilities that go unresolved because they are not made public. Public disclosure of vulnerabilities puts a lot of pressure on manufacturers to fix things, and I guess it’s too hard to do the right thing by keeping the product a person purchases from being used against them.
Hackers use login scripts that automate login attempts that pull credentials from a massive list called a password dictionary that makes breaking into these IoT devices nearly effortless.
While you may feel a peace of mind because you think you are more secure, in reality, you’re making yourself an easy target for surveillance or information disclosure, if your device has a microphone, by people with less than noble intentions.
Case in point.
By searching Server: UBNT Streaming Server v1.2 country:”US” you will find live video feeds that don’t require a login.