RDP stands for Remote Desktop Protocol that is used by people that need to access the desktop of a remote Windows computer. Hackers have been gaining access to these remote machines for over a decade thanks in part to weak passwords that are used to “secure” them by just guessing the username and password. Once hackers gain access, they have all the data that is on that computer, but instead of stealing the data, they are launching ransomware.
Hackers spend most of their time coding with the rest of their time going to looking for low hanging fruit targets which require little effort to place malware and steal data which makes this attack method distinct because of the amount of effort required. Once the attacker has gained access to a computer that has Remote Desktop enabled and accessible to the Internet they place the ransomware and manually execute it. Manual execution is in stark contrast to social engineering where the attacker tricks the user into running malicious payloads that are sent as an attachment in an email that looks like it’s from your bank.
Email is the top choice for attackers that want to spread their destructive toys around the world. The ransomware of yore was a one and done deal where it only infected the computer it was executed on, but WannaCry and NotPetya had worming capability. Once WannaCry or NotPetya was executed on a computer they would replicate themselves across the local network, and sometimes to another network over the Internet if specific ports were open in the firewall.
Ransomware deployed through the Remote Desktop mostly effects small businesses that outsource IT operations or have a lot of work done by contractors. Since Remote Desktop works from any location that has internet and port 3389 open, RDP is ripe for the hacking. Many people and organizations open all ports on their firewall instead of only select ports that are needed for the programs being used on the network.
The average ransom payment demand is $1000, so take the time to properly secure your desktop by using a complex password or turning off Remote Desktop in your settings.
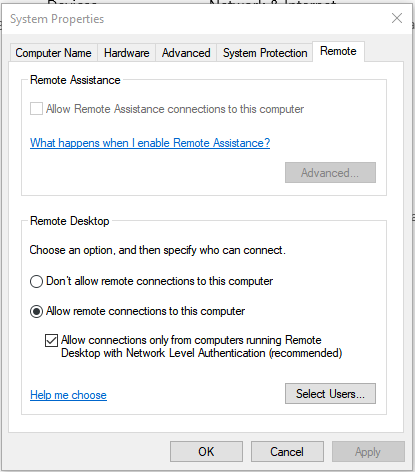
Select “Don’t allow remote connections to this computer” and uncheck “Allow Remote Assistance connections to this computer.” If you use Remote Desktop check the recommended setting of Network Level Authentication, then click “Select Users” and make sure that only the users that need to use Remote Desktop are allowed.