A new antivirus bug called AVGater was discovered by a Vienna, Austria researcher named Florian Bogner. The bug can be exploited by local users only and allows the attacker to have full control over the computer by misusing the restore from quarantine in antivirus. The three access areas of antivirus are the unprivileged domain that consists of the user interface, the SYSTEM that consists of the Windows service, and the Kernel that consists of the operating system kernel (the core of the operating system). The image below depicts the basic functions and communication of antivirus.
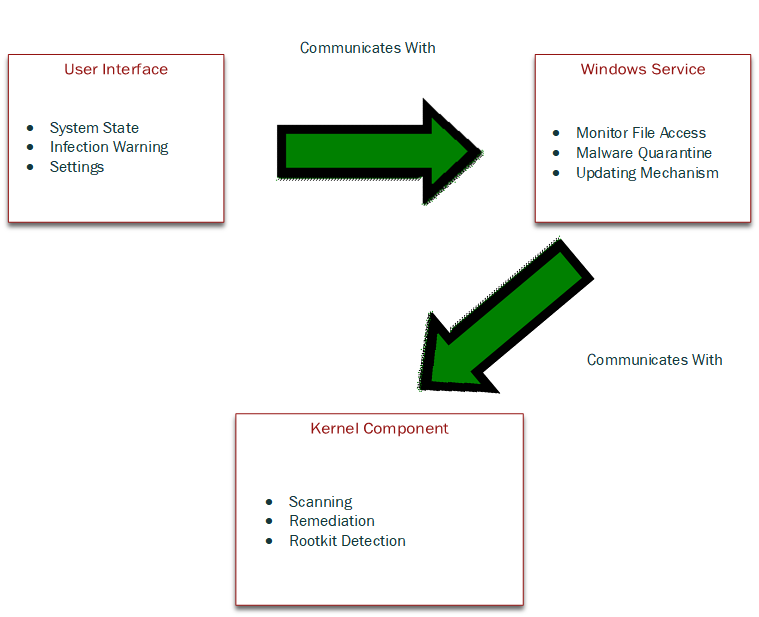
The idea behind this exploit is that an unprivileged user can manipulate the communication channels between the antivirus components, specifically the restore function. You will need some background on Windows terminology before we go further.
- DLL – Stands for Dynamic Link Library, a list of executable functions or data that Windows applications can use
- NTFS – Stands for New Technology File System, is the file structure that Windows uses for storing and retrieving files on your hard drive
- Symbolic Link – a file that points to another file that has contains the requested data
- NTFS Junction – a symbolic link to a folder(s) that acts as an alias of the real folder(s)
How It’s Done
A malicious file is placed on the computer of the target by way of the attackers choosing such as a phishing email or drive-by-download to name a couple. Once the malicious file is placed the antivirus will quarantine the file. The attacker must be local (same network) or convince the user (social engineering) to restore the file to manipulate the restore function to place the malicious file anywhere the attacker wants by using an NTFS junction. The ideal place for restoration is a system folder, e.g., System32 because of the elevated privileges those folders have. NTFS junctions can be made by any user by using the mklink (make link) command. Once the malicious file is restored to the folder of the attackers choosing it can be executed with SYSTEM privileges allowing the attacker to do anything he or she wants with the computer.
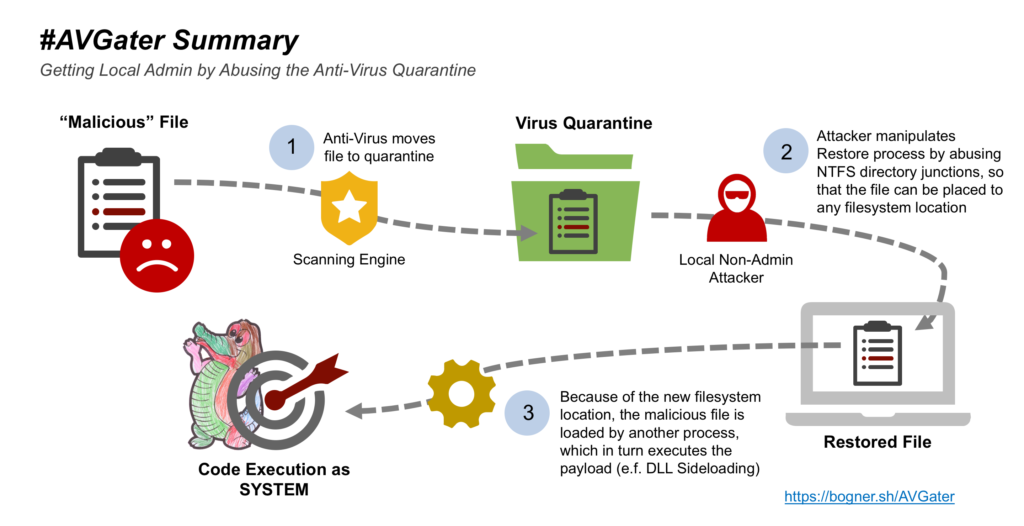
Since the attacker must be local or convince the user to restore the file to manipulate the malware restoration the difficulty of this attack is higher than most attacks and has moderate complexity so the chances an attacker will successfully exploit this bug are low.
Vendors with Issued Patch
- Trend Micro
- EMSISOFT
- Kaspersky
- Malwarebytes
- Zonealarm
- Ikarus
Unaffected Vendors
- Sophos
Vendors with Unknown Status
- Norton
- Bitdefender
- McAfee
- Avast
- AVG
- Avira
- Panda
- There could be many others