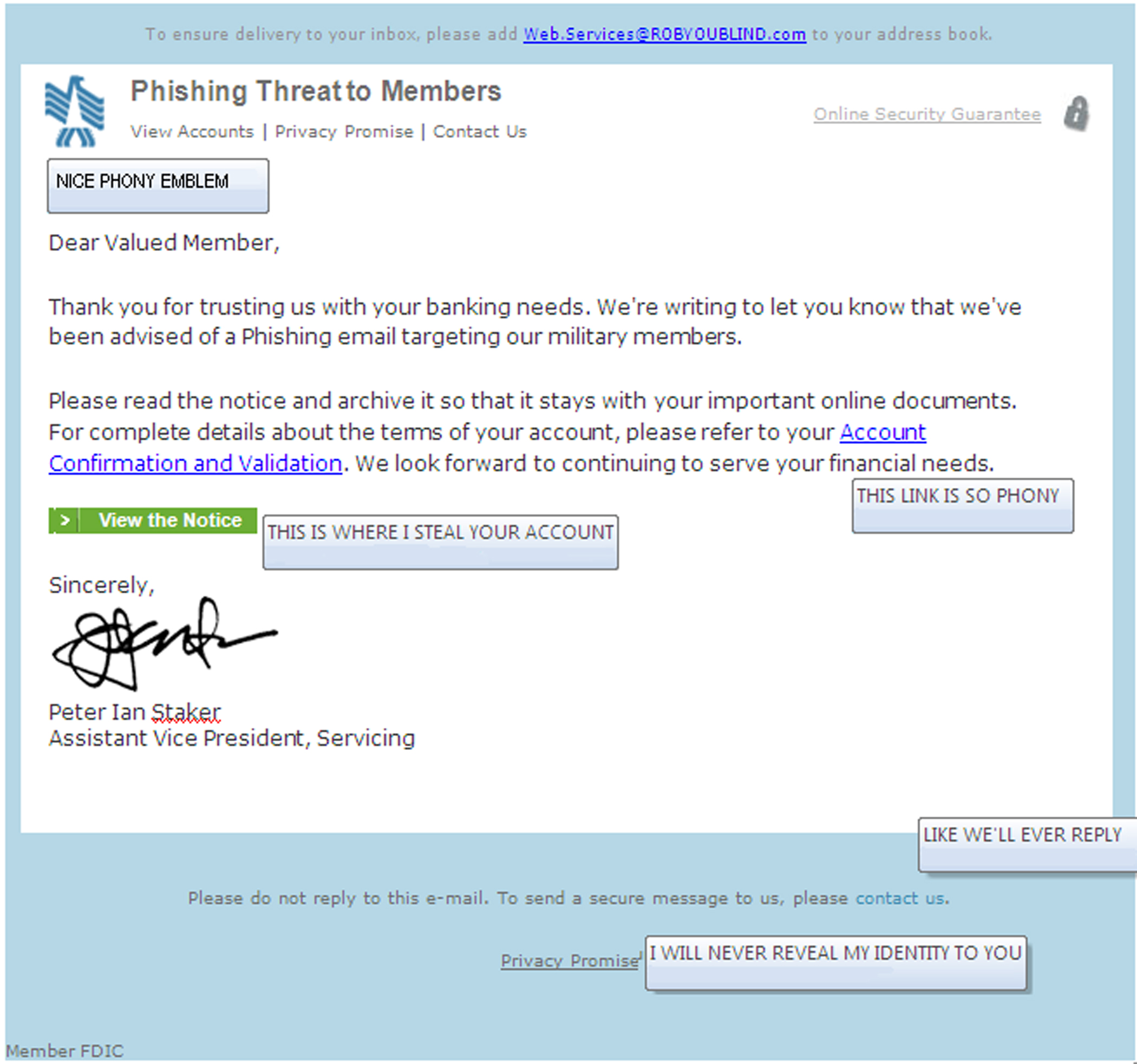
What Can a Hacker Do With Your Email Address?
Email might seem trivial to some people, but if you are active in using the internet to bank, shop, conduct research, ship items, sell items at auction, and a myriad of other activities your life revolves around email. If a hacker were able to take over your email account they could reset passwords to all... Continue reading What Can a Hacker Do With Your Email Address?