A colleague of mine was working on a coworkers personal computer. The job was a fresh Windows 10 installation, and my colleague decided to install Avast Antivirus Free. Shortly after installing Avast Security Onion lit up like a Christmas tree. I didn’t recognize the IP address that the alerts were originating from, so I went into our equipment room where I found the PC plugged in. When I unplugged the ethernet cable, the alerts stopped so I knew I had found the culprit.
Upon initial investigation, I saw that Malwarebytes and Avast were installed. I’ve worked with Malwarebytes in the past and knew that the activity I saw in Security Onion wasn’t typical of it, but I didn’t rule out an altered installer that was retrieved from an untrusted source. I uninstalled Malwarebytes as my first step then I went home because it was the end of the workday. When I came in the next day (Thursday) I saw that there were a few of the same alerts from the previous day, overnight. I chalked the overnight alerts up to Avast then uninstalled it and installed Sophos Home, a far superior product in my opinion.
Just so we’re on the same page, I haven’t used Avast in over a decade because of their bloatware and the tactics used to get you to upgrade to the paid version. Avast has a good signature repository, but with 300,000 new pieces of malware produced daily, they’ve become a one trick pony security solution.
The next day (Friday) I spun up a Windows 10 1803 VM and installed Avast only, then I was quite busy the rest of the day. It wasn’t until Monday that I was able to get back to the VM where I ran a scan manually. The alerts that pop-up during a scan without the advanced features enabled are below.
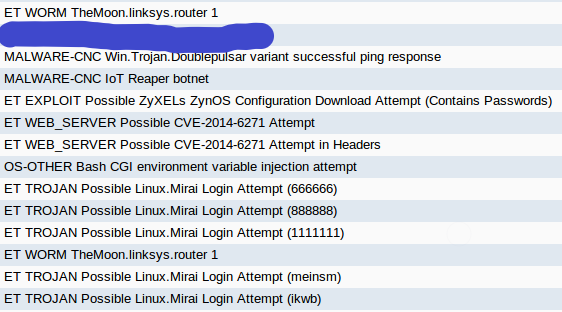
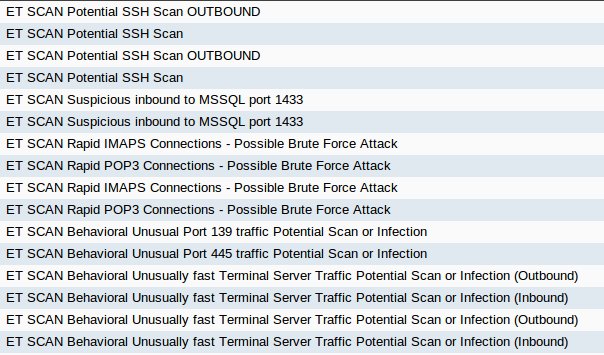
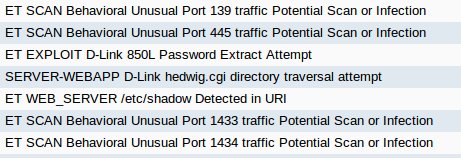
The alerts are a result of a “Network Threat Scan” that is actually an unauthenticated vulnerability scan. The first two times I ran the scan (physical then VM) the same hosts were chosen for testing, but a third scan (second from the VM) chose different hosts except for the network firewall. The method used to decide which host is tested is unknown.
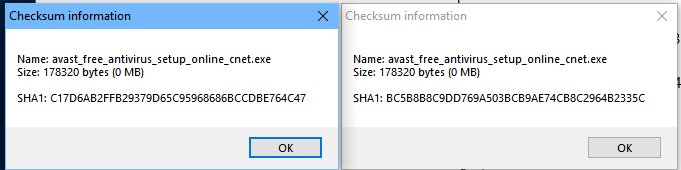
I asked my colleague where he downloaded the Avast installer from and he said that it was an old version from CNET that he had downloaded that day. The thing is, CNET doesn’t carry an old version of Avast. I downloaded the Avast installer from CNET and directly from Avast then hashed them using SHA1. The hashes were different, the installer downloaded from CNET was signed one day and one hour later than the installer downloaded from Avast, and they are the same size, 175KB. Both installers are downloaded and updated from Avast servers.
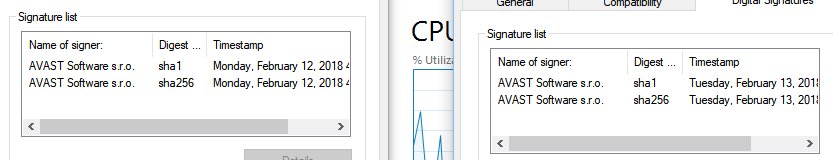
The idea is that any information that you put into a free product will be used to track you and serve advertisements or be sold to compensate for your use of the product.
Surely, a security company wouldn’t do that, right?
Maybe.
I went to the Avast End User License Agreement (EULA) from the Settings -> About Avast menu in the antivirus application where roughly halfway down the page was a link to the privacy policy. Privacy policies are purposely vague to give the company has as much legal leeway as possible when it comes to using your data. Avast is no different.
After clicking on the Privacy Policy link, you’re taken here.
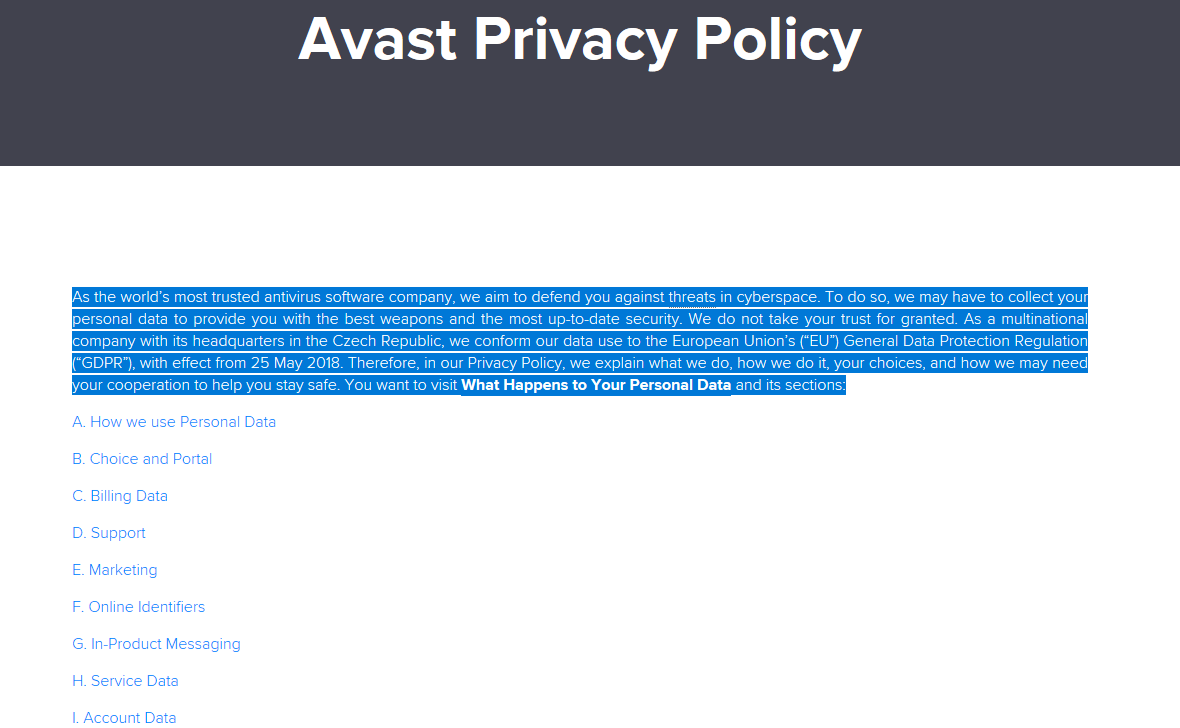
The Privacy Policy begins by describing its purpose, its goal, and limits (vaguely) which none of the language sets off any alarms. Things get interesting in section five paragraph three where it’s stated that third-party ads are delivered to users of their mobile product. Mobile devices are one of the most popular attack vectors and combine that with ad networks being purposely insecure (for the sake of speed and profit) you have a dangerous combination. Their “most trusted” claim in the opening paragraph is starting to look shaky.
So far Avast has said that they collect your personal data to conduct business, deliver services, improve products, etc. all while being GDPR compliant, then they deliver code that immediately executes to your mobile device that contains highly valued and sought after data that ultimately has little protection even when using antivirus.
In the Service Data section, Avast describes what they collect and state that they deanonymize the data they collect about your product usage without any details. I can’t find any reasons why Avast would need vulnerability scan data from your network except to bait you into buying more licenses. Based on the typical person that uses Avast Antivirus Free, they would have no idea how to remediate what the vulnerability scan found other than to spend more money.
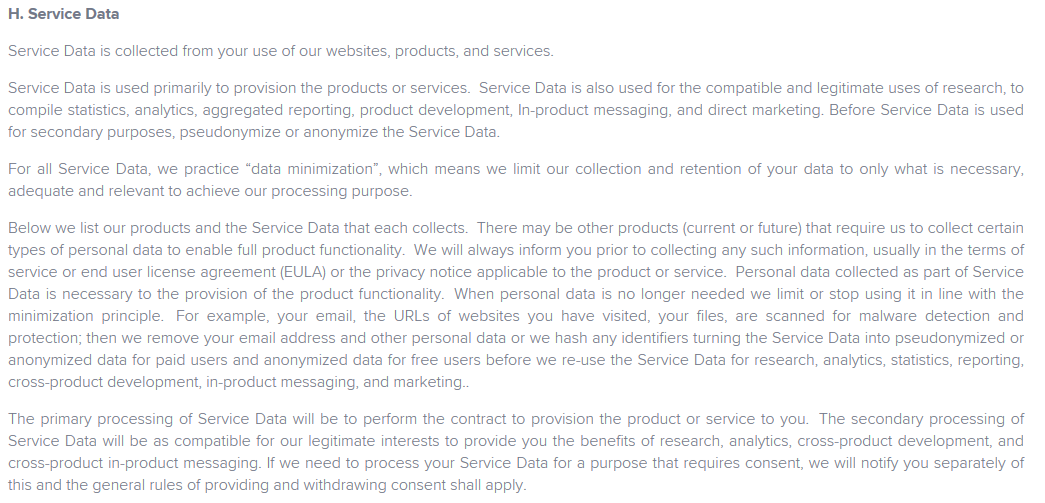
I haven’t been able to find where research is defined which is what I believe they use to collect more data than they need.
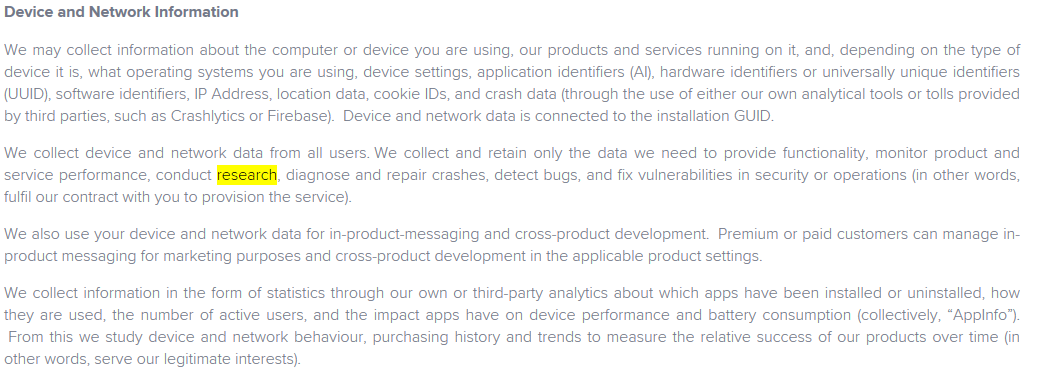
Here’s more research usage without specifics for Device and Network Information, and at the end of the section, they state “serve our legitimate interests” without describing what that is.
I conducted an unscientific poll on Twitter and 91% of respondents said that they wouldn’t be comfortable with Avast having the results on a vulnerability scan.
https://twitter.com/Milwizzle/status/1018905788147032064